Author: Bakhmat M.
The incredible promise of quantum computing comes with a profound security challenge that will impact every business. The eventual arrival of a large-scale quantum computer will render much of today’s encryption obsolete, creating an urgent need for a new standard in digital trust. This transition to Post-Quantum Cryptography (PQC) is not a distant future concern; it is a critical action item for every organization that values data security. Implementing quantum-safe security is the most important cybersecurity upgrade of our generation.
- Key Takeaways for Business and Security Leaders
- What is the Quantum Threat to Current Cybersecurity?
- Why Should We Act Now? The “Harvest Now, Decrypt Later” Problem
- What is Post-Quantum Cryptography (PQC)?
- What is the Path to Quantum-Safe Security? A 3-Step Starter Plan
- Frequently Asked Questions (FAQ)
Key Takeaways for Business and Security Leaders
- Today’s Encryption is Vulnerable: The public-key cryptographic standards (like RSA and ECC) that protect everything from e-commerce to national security are breakable by a future, scaled quantum computer.
- The Threat is Already Here: Malicious actors are engaging in “harvest now, decrypt later” attacks—capturing and storing your encrypted data today with the intent of breaking it with a future quantum computer.
- The Solution is Post-Quantum Cryptography (PQC): PQC refers to a new class of cryptographic algorithms that are resistant to attacks from both quantum and classical computers. These are the standards that will secure our data in the quantum era.
- The Transition Must Start Now: Migrating an entire organization’s cryptographic infrastructure—from applications to servers—is a complex, multi-year process. Waiting until the threat is imminent will be too late.
- Global Readiness is Dangerously Low: Recent industry studies, such as IBM’s Quantum-Safe Readiness Index, show that organizations are just beginning to grasp the scale of this challenge, with an average readiness score of only 21 out of 100.
Colobridge Expert:
As an infrastructure partner, our core mission is to ensure the long-term security and integrity of our clients’ data. The quantum threat shifts the landscape of digital risk management entirely. We are moving from a theoretical risk to a concrete planning scenario. Our role is to help businesses navigate this complex transition pragmatically. The conversation we are having with our clients today is about cryptographic agility—the ability to discover, manage, and upgrade encryption across their entire infrastructure. This isn’t just about algorithms; it’s about making sure your hardware, software, and cloud environments are ready for the change. The journey to quantum resilience begins with a clear-eyed inventory and a strategic plan.
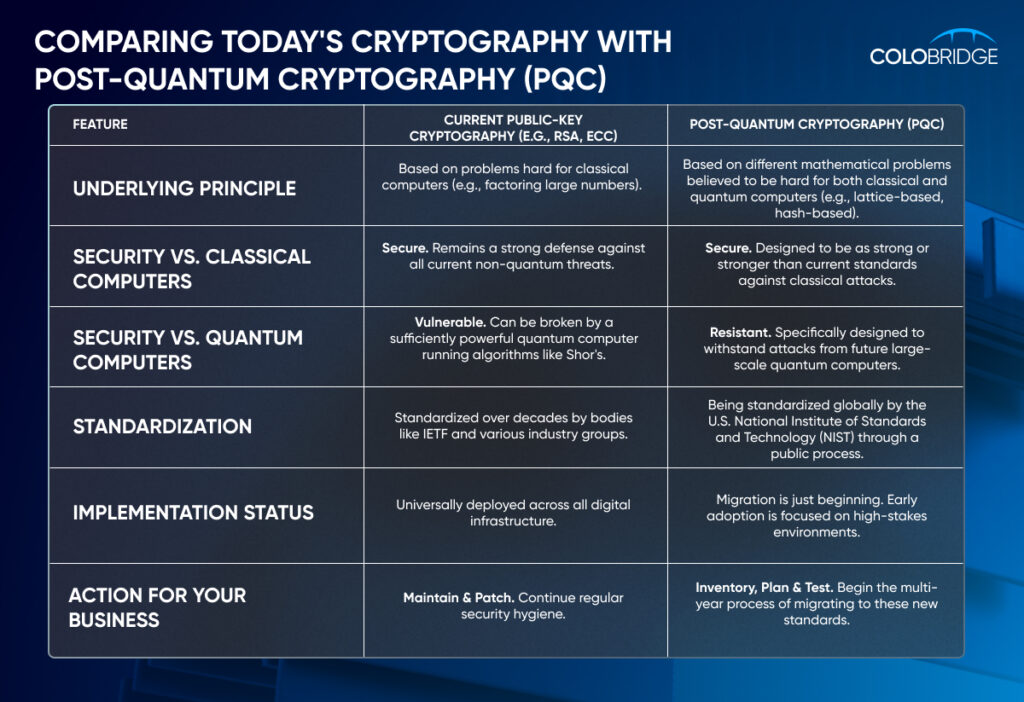
What is the Quantum Threat to Current Cybersecurity?
Modern public-key cryptography relies on mathematical problems that are practically impossible for classical computers to solve. For example, the security of the widely used RSA algorithm depends on the difficulty of factoring extremely large numbers.
A large-scale quantum computer running Shor’s algorithm could solve this factoring problem exponentially faster, effectively breaking the encryption. While today’s quantum computers are not yet powerful enough to do this, the rapid progress in the field, documented by leading research institutions worldwide, makes this a future certainty that businesses must prepare for now.
Why Should We Act Now? The “Harvest Now, Decrypt Later” Problem
The most immediate danger is not that a quantum computer will suddenly break all encryption overnight—the so-called “quantum apocalypse.” The real, present-day threat is data harvesting. Any encrypted communication, trade secret, or piece of classified corporate information sent over the internet today can be intercepted and stored. Years from now, when a capable quantum computer becomes available, this stored data can be decrypted. For data that needs to remain secure for decades—such as health records, financial data, and intellectual property—this threat is not futuristic; it’s active.
What is Post-Quantum Cryptography (PQC)?
To counter this threat, the global cryptography community has been developing Post-Quantum Cryptography (PQC).
PQC does not require a quantum computer to run; it refers to a new generation of cryptographic algorithms that can run on our existing classical computers but are designed to be resistant to attacks from both classical and quantum computers. In 2022, the U.S. National Institute of Standards and Technology (NIST) announced the first set of standardized PQC algorithms after a multi-year international competition, marking a major milestone in the journey toward a quantum-safe future.
What is the Path to Quantum-Safe Security? A 3-Step Starter Plan
The transition to PQC is a marathon, not a sprint. National security guidance in the U.S. requires compliance by 2035, but organizations report that a full migration could take up to 12 years. Action must begin today.
- Inventory: Discover Your Cryptographic Dependencies.
The first step is to identify every system, application, and data store in your organization that relies on public-key cryptography. This “crypto-discovery” phase is often the most time-consuming and is crucial for understanding the scope of the migration. - Plan: Develop a Migration Roadmap.
Once you know what needs to be protected, you can develop a prioritized roadmap. This involves assessing which new PQC algorithms are right for your use cases and planning for a phased rollout, starting with your most sensitive and long-lived data. - Test: Begin Piloting and Experimentation.
Start testing the new NIST-standardized algorithms in non-production environments. Understand their performance characteristics and how they integrate with your existing systems. Working with trusted infrastructure partners can help you create secure sandboxes for this crucial testing phase.
Frequently Asked Questions (FAQ)
1. What is the difference between quantum cryptography and post-quantum cryptography?
They are very different. Quantum Cryptography (like QKD) uses the principles of quantum mechanics to securely distribute encryption keys, often requiring specialized hardware. Post-Quantum Cryptography (PQC) is a set of new mathematical algorithms that run on classical computers and are resistant to being broken by quantum computers. PQC is the direct replacement for today’s vulnerable algorithms like RSA.
2. When will a quantum computer be able to break today’s encryption?
While there is no exact date, many experts in the field, including those cited in reports by organizations like the Global Risk Institute, believe it could be within the next 10 to 15 years. However, because of the “harvest now, decrypt later” threat, the timeline for action is now.
3. Where should my organization start with PQC?
The best place to start is with Step 1: Inventory. You cannot protect what you cannot see. Begin a comprehensive audit of all cryptographic assets in your hardware, software, and services. Engage with your security and infrastructure partners to help build a complete picture of your cryptographic footprint.
4. How can I learn more about the technical aspects of PQC?
For those interested in a deeper technical dive, we recommend exploring the official publications from the NIST PQC Standardization Project. For guidance on preparing your infrastructure, consult with expert partners who specialize in cloud and data center security.





