Cloud security combines policies, practices, approaches and technologies to ensure cybersecurity and protection of applications and data in cloud environments. Detailed access control policies, compliance with industry and corporate security requirements, and the use of automated backup and disaster recovery tools can be the key to protection against external and internal threats.
How Does Cloud Security Work?
Protecting data in public, private, hybrid or multi-cloud is a task for a cloud provider and its client. The client can implement a solid cloud security strategy only if it fully understands its security responsibilities.
Colobridge’s Expert:
“The provider’s obligations to protect client IT infrastructure are set out in a Service-Level Agreement (SLA). В In general, the service provider provides physical security by creating conditions for the hardware to run smoothly (certified data centre built in line with industry standards, access control and management system in the data centre, video surveillance). At the request of our customers, we can install IP locks on the hardware cabinets, activate our firewall, provide aaS access or, under certain conditions, enable data encryption. Secure cloud computing at the legal level, e.g., against unlawful seizure – is ensured by German legislation. We recommend the client to use network controls, multi-factor identification, and pay the utmost attention to application and data access management”.
Cloud computing security directly depends on the cloud model chosen. For example, in IaaS (“Infrastructure as a Service”), the provider creates a secure environment for computing and storage as well as the physical network. The client, in turn, protects the data itself at the level of operating systems and applications, takes care of backups, and conducts information security audits.
Five key approaches to ensuring secure cloud computing:
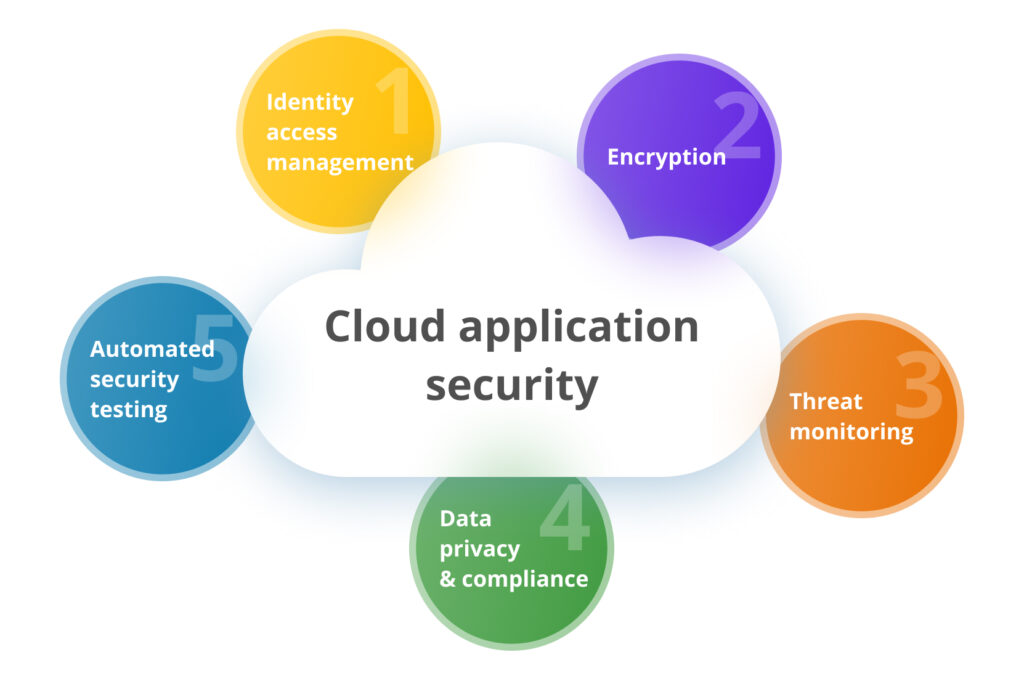
Why Is Cloud Security Important?
New ways to steal, compromise, or destroy data emerge as the cloud computing market grows. Unfortunately, many companies that have migrated data to the cloud overlook data protection and rely heavily on the cloud provider without fully understanding their scope of responsibility. It can have dire consequences, from short-term business interruption to loss of revenue and reputation. While it’s impossible to be fully protected from cyber threats in the cloud, there are many ways to reduce business risks significantly. It’s a key benefit of cloud security as a strategy.
Main Types of Cloud Security Solutions:
- IAM — managing account data for user identification, authentication and access control;
- DLP — specialised software to protect against data leakage in the company;
- SIEM — specialised software for security information management and security incident management;
- PKI — a set of tools for cryptographic protection (the so-called public key infrastructure).
Cloud Security Risks And Challenges
Data stored in the cloud can be affected because of the same reasons as in local IT infrastructure. First of all, this includes leakage or damage to business-critical information, phishing, malware infection, DDoS attacks, competitors, and former or current employees stealing commercial information.
Why is it difficult for many companies in general to ensure data security in cloud computing:
- the company has not developed its own strategy and tools for enhanced data control and management in the cloud environment;
- simple or default passwords are used, and multi-factor authentication is disabled;
- access policies for different categories of data depending on their importance have not been developed;
- outdated security tools are used or sporadically updated;
- data encryption and other solutions that enhance data security in the cloud are not connected.
Get in touch with Colobridge technical experts to learn how to protect your data in the cloud. Use our expertise to design and deploy a flexible, reliable and secure IT infrastructure tailored to your business, current and future workloads, budget, security requirements and other factors.





